How Organizations Successfully Build Security and Compliance Programs
For many organizations, the compliance journey does not start with an audit or a certification goal. It starts much earlier and much more informally.
It often begins with well-intentioned security practices, unclear ownership, and growing uncertainty about what customers, partners, or prospects actually expect. There may be capable teams and good instincts in place, but little structure tying everything together.
Moving from informal practices to a defined and defensible security and compliance program is one of the most important transitions an organization will make. When approached thoughtfully, it creates clarity, builds trust, and supports long term growth. When rushed or handled out of sequence, it often leads to frustration, rework, and unnecessary cost.
What follows reflects what we consistently see when helping organizations build security and compliance programs for the first time. It is a practical view of what works, what does not, and how successful programs are built to last.
What “0 to 1” Really Means
In practice, “0” usually means security and compliance exist, but only informally. Processes live in people’s heads. Controls are applied inconsistently. Customer security questions are handled reactively. Ownership is unclear.
Reaching “1” does not mean perfect security or formal certification. It means governance is defined, risks are formally assessed, controls are documented and aligned to a framework, execution is consistent, and the organization can clearly explain and demonstrate its security posture to customers, auditors, and third parties.
At this stage, success looks like a program that is understandable, repeatable, defensible, and able to grow with the business.
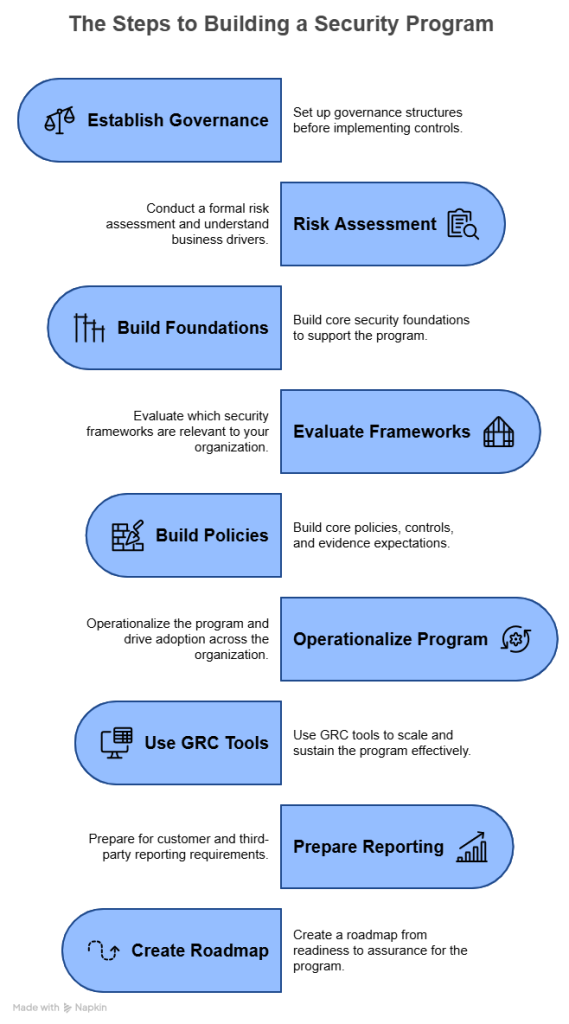
Step 1: Establish Governance Before Controls
One of the most common challenges we see is organizations focusing on policies, tools, or certifications before establishing governance. Governance determines who owns security and compliance, how decisions are made, and how accountability is enforced.
Early success usually includes identifying an executive sponsor, even if security is not yet a full time role. It also means clearly defining responsibility for security and compliance activities, documenting how risks and exceptions are approved, and establishing escalation paths.
Without governance, even well-designed controls tend to erode over time.
Step 2: Perform a Formal Risk Assessment and Understand Business Drivers
Before selecting a framework or writing policies, organizations need to understand why compliance is being pursued and where real risk exists.
In most cases, the initial driver is external. Customer questionnaires, enterprise procurement requirements, investor expectations, or sales delays tied to SOC 2, ISO, or industry-specific requirements often trigger the process.
Successful programs formalize this understanding through an initial, documented risk assessment. This includes identifying key risks, evaluating their likelihood and impact, and determining how those risks will be treated or accepted. The risk assessment becomes the foundation for control selection and prioritization.
Programs grounded in documented risk and real business drivers are far more effective and far easier to sustain.
Step 3: Build Across Core Security Foundations
Strong security and compliance programs are not built around a single policy or framework. In practice, they consistently address a common set of foundational security domains that mature over time.
While implementation depth may vary, most successful programs address the following areas early in the journey:
- Governance, risk management, and compliance oversight
- Identity and access management
- Data protection and privacy
- Asset and configuration management
- Security operations and incident response
- Vendor and third-party risk management
- Security awareness and training
- Business continuity and resilience
Addressing these areas incrementally ensures the program reflects real security maturity rather than surface-level compliance.
Step 4: Evaluate Which Frameworks Are Relevant
Not every organization needs every framework, especially early on. Choosing the right starting point is one of the most important foundation decisions.
Common frameworks and standards we see at this stage include SOC 2 for customer trust and vendor risk management, ISO 27001 for a globally recognized information security management system, ISO 27701 for privacy, ISO 42001 for organizations addressing AI governance, NIST based frameworks for U.S. regulatory alignment, PCI DSS for organizations handling payment card data, and HITRUST for healthcare and other regulated environments.
While these frameworks serve different purposes, most share common control themes. This allows organizations to build foundational controls once and map them across multiple frameworks as requirements evolve. Selecting a framework should be based on customer expectations, industry norms, data types, geographic footprint, and long-term business goals.
Getting this decision right early helps organizations avoid rebuilding controls later.
Step 5: Build Core Policies, Controls, and Evidence Expectations
Once governance, risk, and framework direction are established, the next step is formalizing the program. This is where informal practices become documented, repeatable, and defensible.
Foundational elements typically include information security policies, access control processes, incident response planning, vendor risk management, change management, and security awareness training. Just as important is defining how evidence will be created, maintained, and reviewed.
In our experience, many first time programs struggle not because controls do not exist, but because there is no reliable way to demonstrate that those controls are operating consistently.
Step 6: Operationalize the Program and Drive Adoption
A compliance program only works if it is embedded into daily operations. This is often where the difference between paper compliance and real maturity becomes clear.
Operationalizing the program means integrating security into onboarding and offboarding, applying access controls consistently, tracking remediation activities, and periodically reviewing risks and controls. It also requires change management. Teams need to understand why controls exist, not just what they are expected to do.
Programs that focus only on documentation rarely hold up under scrutiny.
Step 7: Use GRC Tools to Scale and Sustain the Program
As organizations mature, spreadsheets and shared folders often stop being sufficient. This is where governance, risk, and compliance tools can provide meaningful value.
When introduced at the right time, GRC tools help centralize controls, clarify ownership, streamline evidence collection, and support ongoing monitoring. They reduce manual effort, improve consistency, and make it significantly easier to respond to customer questionnaires and audits. GRC platforms also allow organizations to map controls across multiple frameworks without duplicating work.
Technology should support an established process, not replace one. Organizations that see the greatest benefit from GRC tools are those that invest first in governance, risk assessment, and control design, then use technology to scale and sustain the program.
Step 8: Prepare for Customer and Third-Party Reporting
Once a compliance program takes shape, external reporting expectations follow quickly. Customers, partners, and other third parties may request security summaries, completed questionnaires, policy documentation, or clarity on readiness toward SOC 2, ISO, PCI, or HITRUST requirements.
Organizations with a documented, operational program and centralized evidence are far better positioned to respond efficiently and consistently. Planning for reporting early reduces disruption, shortens sales cycles, and builds trust.
Step 9: Create a Roadmap From Readiness to Assurance
Moving from informal practices to a mature program is not about doing everything at once. It is about building a strong foundation and defining a clear path forward.
A roadmap outlines near-term readiness goals, identified gaps, remediation timelines, and longer-term assurance objectives such as SOC 2 reports, ISO certification, PCI validation, or HITRUST assessment. A clear roadmap is part of the foundation itself because it ensures early decisions support future assurance rather than limiting it.
Common Pitfalls We See at This Stage
Many organizations encounter avoidable challenges during this phase. Common issues include selecting frameworks based on assumptions rather than confirmed customer needs, purchasing tools before defining processes, and treating compliance as a one time project instead of an ongoing program.
Other frequent challenges include unclear ownership, weak risk assessment practices, insufficient evidence collection, and attempting to pursue attestation before readiness is achieved. Recognizing these patterns early can save significant time and effort.
Who This Journey Is Most Relevant For
This stage is especially common for growing technology and SaaS organizations, companies entering enterprise sales cycles, healthcare and fintech organizations facing regulatory pressure, and businesses formalizing security and compliance for the first time due to customer or investor expectations.
Starting from informal practices is normal. What matters is building the program thoughtfully and in the right order.
Why Many Organizations Choose to Work With a Consulting Partner
Building a security and compliance program from scratch requires coordination across teams, familiarity with frameworks, and a clear understanding of assurance expectations. For many organizations, internal teams do not have the time or specialized experience to do this efficiently while maintaining daily operations.
In practice, the most successful first time programs share one common trait. They benefit from experienced guidance that helps teams make the right decisions early, avoid false starts, and build a foundation that supports growth rather than constrains it.
CompliancePoint works with organizations at every stage of the compliance lifecycle, helping them move from informal practices to audit ready programs with confidence. If you are beginning this journey and want guidance from a team that has done this many times before, reach out to connect@compliancepoint.com to start the conversation.
Finding a credible expert with the appropriate background, expertise, and credentials can be difficult. CompliancePoint is here to help.