The Keys to an Effective SOC 2 Readiness Assessment
A SOC 2 readiness assessment is a key step on the journey to achieving SOC 2 compliance. Think of the readiness assessment as a dry run before your actual SOC 2 audit. An auditor will review your requirements and controls and notify your organization of any compliance gaps that need to be addressed before the audit. The corrections that are made, or not made, will play a major role in the success of your report.
To get valuable knowledge out of your assessment, some vital tasks and important decisions need to be handled ahead of time, including:
Identify the Appropriate SOC 2 Trust Services Principles
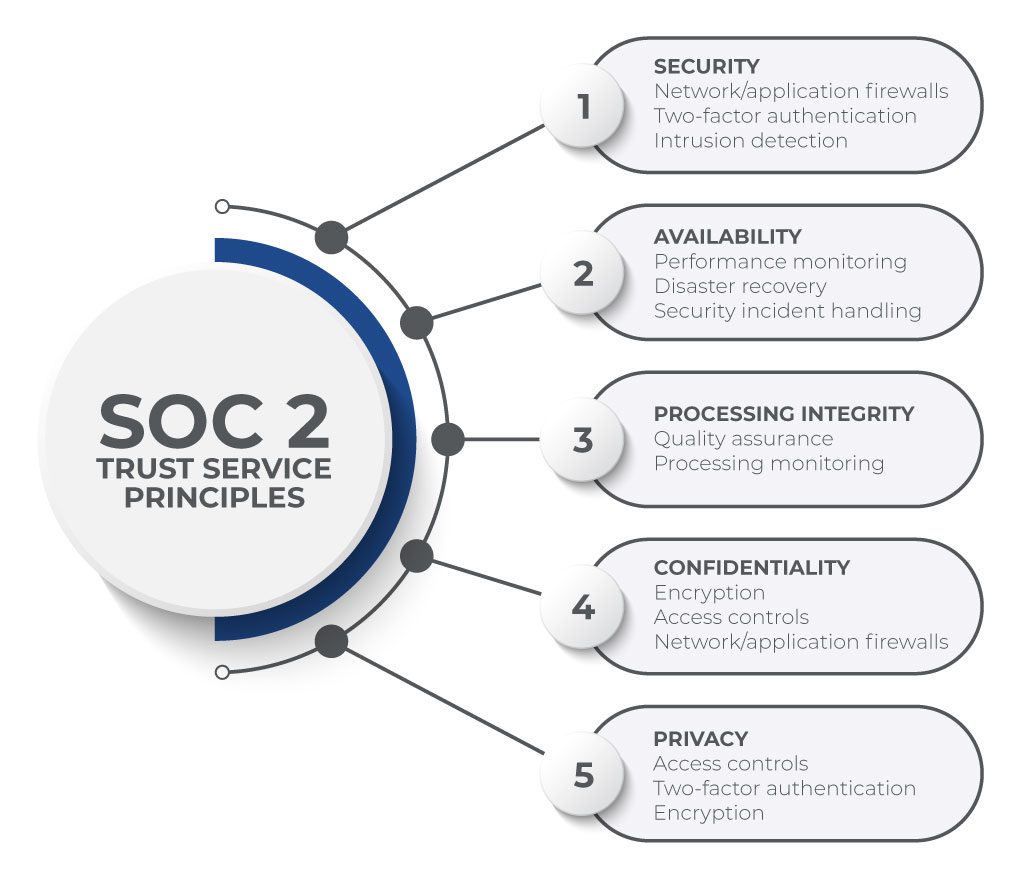
The SOC 2 standard is based on the 5 Trust Services Principles: Security, Availability, Confidentiality, Processing Integrity, and Privacy. All organizations must meet the requirements of the Security principle. When crafting a scope, organizations need to identify which of the remaining principles are relevant to their operations. Most organizations will need to include the Confidentiality principle in their scope.
Have Controls in Place
Typically, a SOC 2 readiness assessment is conducted with the assumption that you have at least some controls, policies, and procedures implemented and documented. This allows the assessor to evaluate how well what you have in place meets the Trust Service Criteria.
If you do not have enough of a program in place to truly evaluate, it may make more sense to establish a Security Policy, a set of controls that fit your operation, and start documenting key procedures. CompliancePoint can help you design a program to prepare for a readiness assessment that would include controls design, and policy and procedure consulting. Be aware that many companies do not consider ‘the basics’ part of a SOC 2 readiness assessment.
Type 1 Report vs Type 2 Report
Before a SOC 2 readiness assessment, your organization needs to know if it wants a Type 1 or a Type 2 report. Here’s a comparison of the two options to help clarify the decision.
The Differences
The SOC 2 Type 1 report assesses your compliance at a single point in time and provides an opinion on the Controls Design only and not the implementation effectiveness. The Type 1 report is an audit to determine if your organization has documented controls implemented that meet the Trust Services Principles. This report can be completed in a matter of weeks.
The SOC 2 Type 2 report assesses the effectiveness of your organization’s security controls over a period of time (typically a window of 6-12 months) and provides an opinion (attestation) on both the controls’ design and operating effectiveness. An initial type 2 report can take up to a year to complete and may cost more than a Type 1 report.
The Similarities
Both report types require an audit by a certified public accountant (CPA) firm affiliated with the American Institute of CPAs (AICPA).
The Deciding Factors
The Type 2 report is more comprehensive as it goes more in-depth into the effectiveness of the security controls. Compared to the Type 1, a Type 2 report provides a higher level of confidence in your security controls for you and your customers. Organizations may find that many clients require a Type 2 report to do business together.
Despite being the report that provides the lesser amount of assurance, a Type 1 report does make sense in certain circumstances. For organizations just beginning their SOC 2 journey, Type 1 allows the company to focus on creating a manageable set of controls with a much lower risk of control failures. Once the controls design is approved by the auditor in the Type 1 report, the organization can then mainly focus on operational effectiveness for their Type 2. A Type 1 report shows SOC 2 compliance and can serve as a foundation for a Type 2 report in future audits. If your organization finds itself needing to prove SOC 2 compliance quickly to secure new business, the Type 1 report is a valuable option to have at your disposal.
Documentation
Gather all the documentation you’ll need for the SOC 2 readiness assessment and audit, including:
- Asset inventory
- Policies and procedures
- Response plans
- System descriptions
CompliancePoint has a team of experts that can put your organization on the path to SOC 2 compliance and prepare for a successful audit. Contact us today at connect@compliancepoint.com to learn more about how we can help.
Finding a credible expert with the appropriate background, expertise, and credentials can be difficult. CompliancePoint is here to help.





