The Phish Scale: A New Email Classification System Introduced by NIST
According to the most recent Verizon Data Breach Report, breaches due to phishing attacks are down 6.6% since 2019. However, phishing continues to be an area of concern for information security professionals. Even as click rates are at the lowest (approximately 3.4%, according to Verizon), research from IBM has found that phishing is still the root cause of at least 14% of all data breaches. Organizations have taken notice and are increasing their integration of anti-phishing training and tools. However, it is important to understand that the sophistication of phishing attacks is also increasing, and the tools and methodologies you use need to advance with them.
CompliancePoint has been called in to conduct forensic investigations on several cyber incidents in the past few years that originated from phishing attacks. During past investigations, we noted the tendency of the malicious emails to contain broken English and originate from unknown senders. There were many common context clues that affected users could have easily picked up on, with appropriate training. In 2020, even with the new low click rate, CompliancePoint has continued to see phishing as a point of origination for attacks. However, as we analyze the reasons behind the success of these new attacks, we see improvements in the emails themselves. Successful phishing emails now appear to originate from within the organization or from known contacts. There are no errors in spelling or grammar, and the subject matter of the email is relevant to the individuals who unfortunately open the document or click the link. These trends are why the National Institute of Standards and Technology (NIST) has now published the “Phish Scale.”
The Phish Scale uses a rating system for phishing cues and premise alignment to gauge the difficulty of identifying the legitimacy of the email. The number of cues identifiable in a phishing email, such as errors and technical indicators, are counted to determine cue difficulty. The premise is then rated as high, medium, or low based on the alignment of the message content with a target audience (for example, alignment with work responsibilities and business practice plausibility). The Phish Scale then evaluates the number of cues utilized with the premise alignment rating to determine the overall difficulty.
The Phish Scale
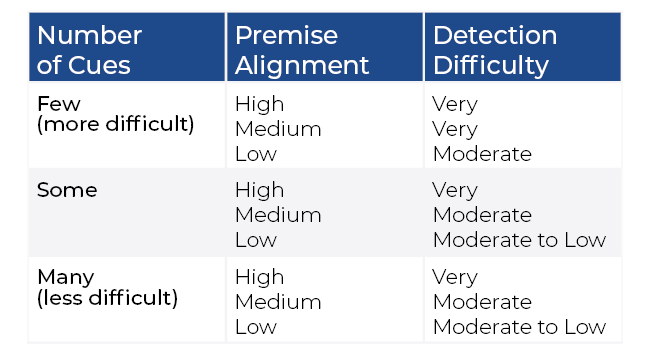
Low click rates during anti-phishing campaigns, without additional context, can result in a false sense of security. According to NIST, the Phish Scale program is intended to help provide that context, helping security professionals develop a deeper understanding of WHY some users click. The Phish Scale provides the necessary information to determine the difficulty of detecting a malicious email and whether the email should be easier or harder for a particular target audience to detect. This context can help CISOs determine the best types of training to provide.
Although additional research is needed (and underway), the NIST article, published in the Journal of Cybersecurity, provides an excellent Do-It-Yourself tool description and methodology for those of us concerned about the increased sophistication of phishing. If you do not currently use an anti-phishing tool, this is a great start. If you do, it is also important to evaluate the capabilities of your tool to provide the knowledge and insights needed to address any threats.
If you’d like more information or to discuss your organization’s cyber security needs, please contact us at Connect@CompliancePoint.com.
Finding a credible expert with the appropriate background, expertise, and credentials can be difficult. CompliancePoint is here to help.





