CMMC Phase 1 is Here
November 10, 2025, marked the beginning of Phase 1 of Cybersecurity Maturity Model Certification (CMMC). The Department of Defense (DoD) can now require contractors and subcontractors in the defense industrial base (DIB) to conduct a Level 1 or Level 2 self-assessment to be eligible for DoD contracts.
CMMC Level 1 and Level 2
CMMC Level 1 applies to organizations that handle Federal Contract Information (FCI) but not Controlled Unclassified Information (CUI). All organizations seeking a Level 1 certification can conduct a self-assessment.
Organizations seeking a Level 2 certification can only self-assess if they are handling FCI and/or non-prioritized CUI. This will likely only be a small percentage of Level 2 organizations. Organizations handling “prioritized” or “critical” CUI are not allowed to perform a self-assessment for their Level 2 certification. They must have a certified third party (C3PAO) conduct their assessment. CMMC Phase 2, which starts November 10th, 2026, will implement third-party assessment requirements. Organizations expecting to fall under level 2 should begin establishing relationships with a C3PAO now.
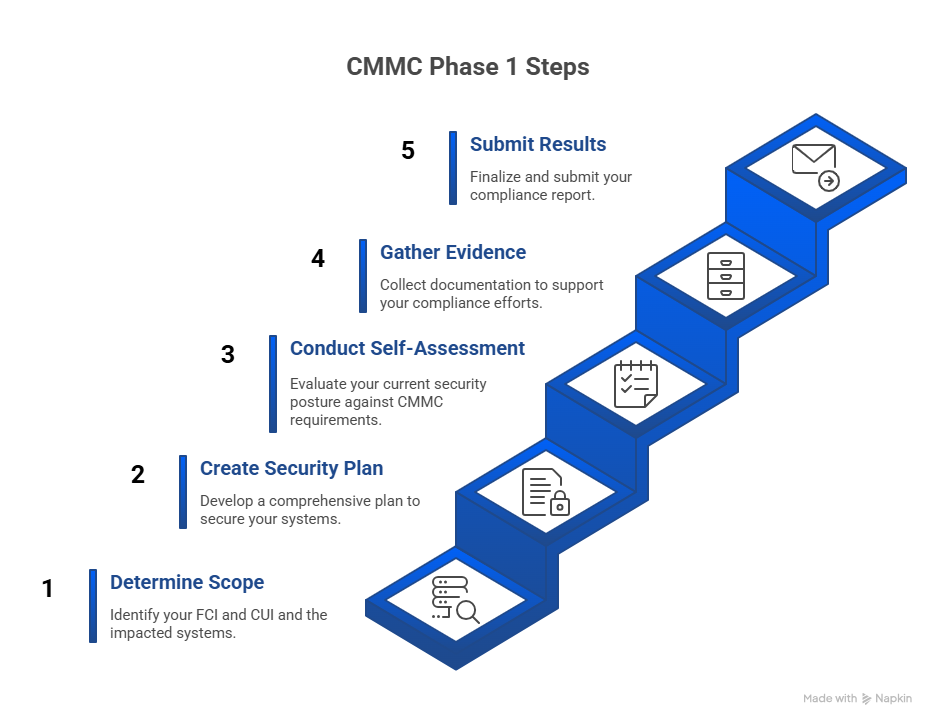
CMMC Phase 1: What Actions to Take Now
If your business currently holds DoD contracts or plans on bidding on them in the future, it needs to act now to demonstrate CMMC compliance. Here are some steps organizations can take within the Phase 1 period.
Determine Scope and Applicability
Determine if your contracts include the processing, storage, or transmission of FCI or CUI. If they do, CMMC applies to your organization. The types of CUI the organization handles will determine if Level 2 or Level 3 is the appropriate CMMC certification. Level 3 applies to organizations accessing CUI for high-priority DoD projects.
Identify all systems, personnel, and subcontractors that come into contact with the FCI and CUI. Those will be the subject of your assessment.
Create a System Security Plan
A System Security Plan (SSP) is a required document that describes an organization’s security controls and how they protect FCI and CUI. SSPs typically include details on system boundaries, system interconnections, implemented security controls, and the environment in which the system operates.
Conduct the Self-Assessment
For organizations targeting CMMC Level 1 certification, they must assess that they comply with the 15 Federal Acquisition Regulation (FAR) 52.204.21 cybersecurity requirements:
- Limit information system access to authorized users
- Limit information system to the types of transactions and functions that authorized users are permitted to execute
- Verify and control/limit connections to and use of external information systems
- Control information posted or processed on publicly accessible information systems
- Identify information system users, processes acting on behalf of users, or devices
- Verify the identities of those users, processes, or devices as a prerequisite to allowing access to organization information systems
- Sanitize or destroy information system media containing FCI before disposal or release for reuse
- Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals
- Escort visitors and monitor visitor activity; maintain audit logs of physical access; control and manage physical access devices
- Monitor, control, and protect organizational communications
- Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks
- Identify, report, and correct information and information system flaws in a timely manner
- Provide protection from malicious code at appropriate locations within organizational information systems
- Update malicious code protection mechanisms when new releases become available
- Perform periodic scans of the information system and real-time scans of files from external sources
When evaluating, determine if each control is fully implemented, partially implemented, or not implemented. Prioritize remediating any controls scored as partially or not implemented. For Level 1 assessments, controls are given a pass/fail score.
Download the Level 1 Self-Assessment Guide before starting.
Organizations striving for Level 2 certification must assess themselves against the 110 controls found in NIST 800-171. Score your controls using the NIST SP 800-171 Assessment Methodology.
For any controls that are not properly implemented, document them with a Plan of Action & Milestones (POA&M). A POA&M is used to track and manage the remediation of controls that don’t meet the standards of CMMC compliance. It details the tasks, resources, and timeline (maximum of 180 days) for remediating vulnerabilities identified during the assessment. POA&Ms are not allowed for Level 1.
Gather Evidence
Regardless of which certification level applies to your organization, be sure to gather the evidence necessary to demonstrate compliance with each control. Evidence can include policy documents, screenshots, configuration records, logs, training records, etc.
Record and Submit Your Results
Once your self-assessment is complete, submit your score to the Supplier Performance Risk System (SPRS). Be sure to include:
- The assessment score
- The date of completion
- POA&M completion date (if applicable)
- Level of compliance
Maintaining your SPRS record is now a requirement for many DoD contracts. Keep it current and ensure updates are made after major security changes or annual reviews.
CompliancePoint has certified CMMC professionals on staff who can walk you down the path to a successful CMMC certification. Reach out to us at connect@compliancepoint.com to learn more about our services.
CMMC Scoping and Self-Assessments Podcast
To learn more about achieving CMMC certification, watch our CMMC Scoping and Self-Assessment podcast episode below.
Finding a credible expert with the appropriate background, expertise, and credentials can be difficult. CompliancePoint is here to help.





