Common Cloud Misconfigurations and Their Compliance Implications
Modern cloud platforms deliver speed and flexibility, but the environments are complex and often create new security risks. From accidentally exposed storage buckets to weak authentication controls and insufficient audit logging, cloud misconfigurations are a common cause of security incidents and compliance failures. In this blog, we’ll explore several of the most common cloud misconfigurations, how they can lead to data breaches, and put your compliance with regulatory frameworks at risk.
Publicly Accessible Storage
One of the largest examples of a misconfiguration in the cloud today is accidental or inadvertent public access. Let’s first examine how cloud service providers offer many ways to store data:
- Object storage: Examples include Amazon S3, Google Cloud Storage, Azure Blob Storage, and IBM Cloud Storage.
- File storage: Examples include Amazon EFS, Google Cloud Filestore, Azure Files, Dropbox, Box, Google Drive, and iCloud.
- Block storage: Examples include Amazon EBS, Google Persistent Disk, Azure Disk Storage, IBM Cloud Storage, DigitalOcean, and Oracle Cloud Infrastructure Block Volume.
- Databases: Examples include Amazon Aurora, Amazon DynamoDB, Google Cloud SQL, Google Bigtable, Azure SQL, Azure Cosmos DB, Snowflake, MongoDB Atlas, IBM D2, and Oracle Database.
Regardless of the type of cloud storage an organization chooses, access controls are a primary way to ensure the confidentiality of data stored within these platforms. With the increased complexity of cloud configurations, it becomes easy for IT administrators to inadvertently make files and data publicly accessible. The intricacies of automated cloud deployment mechanisms like autoscaling, infrastructure as code (IaC), and continuous integration/continuous deployment (CI/CD) pipelines, also cause rapid changes to occur within cloud environments that can alter initially hardened systems and services. Configuration drift, whether caused by human error or automation, is a real problem, and it happens more often than most organizations realize.
The compliance implications of unintended public access largely depends on the type(s) of data the organization stores within the cloud and what federal, state, or local regulations apply to their industry. Regardless of industry or regulatory framework, the loss, compromise, or unauthorized disclosure of sensitive information is defined as a data breach. Let’s explore some common data breach concerns for different industries:
- For healthcare organizations that store electronic Protected Health Information (ePHI) in the cloud, failure to protect this information from becoming public is considered a violation of HIPAA and can result in monetary penalties and severe damage to an organization’s reputation.
- For organizations that store or process certain credit card information, defined as cardholder data (CHD) by the Payment Card Industry Security Standards Council (PCI SCC), failure to protect this type of information can also result in monetary fines that compound based on the duration of non-compliance.
- Organizations doing business in the European Union or the state of California are often subject to regulations such as the GDPR and the California Consumer Protection Act (CCPA), which require organizations to secure Personally Identifiable Information (PII).
Limited Event Visibility
Not all cloud misconfigurations result in a data breach or rise to the level of public reporting. Still, security misconfigurations can hamper an organization’s ability to achieve or maintain security attestation or certification. Insufficient or underutilized audit logging and monitoring capabilities are common misconfigurations that occur with cloud environments. While cloud providers such as AWS, Google, and Microsoft offer a plethora of security monitoring services, these are often underutilized. So much so that this particular misconfiguration continues to be included in the Online Worldwide Application Security Project (OWASP) published Top 10 Application Security Risks, despite continued advancements in monitoring capabilities through AI and Machine Learning integrations.
The compliance implications for insufficient logging are wide-ranging. Organizations that wish to demonstrate a mature security posture will often opt to undergo audits designed to achieve attestation or certification using a particular framework. These include HITRUST, PCI DSS, CMMC, ISO 27001, and SOC 2, to name a few, all of which have specific domains or sets of controls dedicated to secure audit logging and monitoring capabilities. The inability to prove efficient logging and monitoring can result in a failed audit, which in turn jeopardizes attestation or certification.
Authentication Weaknesses
Another common cloud misconfiguration with security and compliance consequences involves authentication and authorization. This misconfiguration, also found in the OWASP Top 10 under the header “Authentication Failures,” continues to trouble cybersecurity and IT staff across many industries. Several reasons for this include the following:
- Complexity of Implementation: Username/Password, Single Sign On, and leveraging Third Party Identity Providers are all ways to authenticate a userbase or workforce, but authentication architecture can be complex and cumbersome to implement.
- Lack of MFA Support: Even if your organization designs a secure authentication architecture centered around the principle of Multi-Factor Authentication (MFA), not all SaaS applications support MFA or the method of MFA you have implemented.
- Conflicting Guidance on Secure Password Policies: For decades, password complexity and forced rotation requirements were at the center of compliance guidance. Lately, security researchers have begun to shift away from recommending such in favor of utilizing long passphrases. Microsoft and the National Institute of Standards and Technology (NIST) are among the security organizations that have updated their guidance on this subject. Still, you will find password rotation recommendations in many utilized frameworks and published security research papers today, leaving the industry in a bit of a deadlock.
- Many Attacks Focus on the Authentication Chain: From brute force and credential stuffing, to social engineering, to Man in the Middle (MitM) attacks, malicious actors focus on exploiting vulnerabilities or flaws within the authentication chain to gain access.
Authentication failures can result in data breaches, audit failures, ransomware exploitation, lateral movement, you name it. If a malicious actor can get into your network with valid credentials, the security and compliance ramifications are just about limitless.
Best Practices to Avoid Misconfigurations
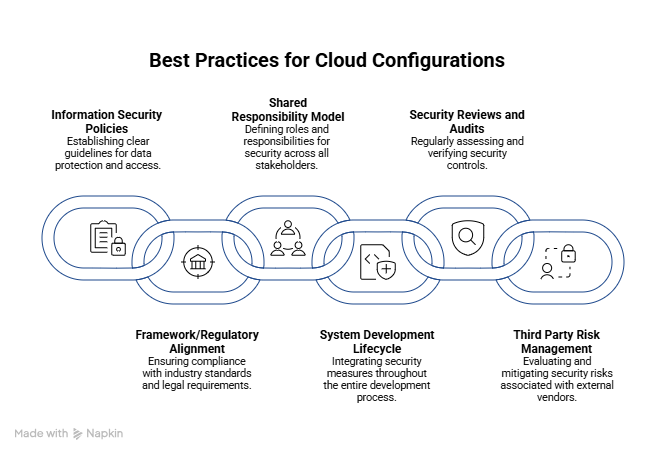
Often, misconfigurations are caused by a lack of governance or security design that allows technical misconfigurations to cause compliance issues. Here is a list of best practices to avoid common root causes of cloud misconfiguration.
- Information Security Policies: Maintaining a set of information security policies is essential in defining the organizational strategy to reduce risk exposure, ensure regulatory compliance, and provide a consistent framework for protecting sensitive data and systems from evolving threats.
- Framework/Regulatory Alignment: In order to ensure your cloud environments, systems and services, and organizational processes are designed properly, you first need to align them to a regulatory framework. Industry-specific frameworks and regulations are a starting point, but additional guidance may be needed. Some frameworks focus on protecting specific types of data, while others focus on organizational processes.
- Understand the Shared Responsibility Model: Cloud service providers publish shared responsibility models that outline what the provider is responsible for versus your organization utilizing the environment. Generally speaking, the provider is responsible for the security of the cloud, whereas your organization is responsible for the security of data in the cloud. However, this is made more complex in practice with SaaS, IaaS, and PaaS business models. Make sure that for every cloud system or service deployed, there are clearly defined responsibilities.
- System Development Lifecycle (SDLC): A mature SDLC program will not only address the creation, hardening, and deployment of information systems but also define how these systems and services allow an application to achieve business objectives securely.
- Security Reviews, Assessments, and Audits: The best way to understand if your organization is following security best practices and adhering to compliance requirements is to check your work! This may come in the form of an internal security review that focuses on a targeted area (such as access & permissions), an assessment designed to measure the effectiveness of security controls, or an audit to verify compliance with a specific standard or regulation.
- Third Party Risk Management: Organizations often rely on a web of third parties to perform tasks in the cloud, such as Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) that have permissions, capabilities, and processes that can impact the security of your cloud environment. Make sure your organization understands what vendors have access to, defines their responsibilities accordingly, and manages the risks associated.
CompliancePoint has a team of experienced professionals that can help your organization with all aspects of cybersecurity and regulatory compliance, including cloud security. Reach out to us at connect@compliancepoint.com to learn more about our services.
To learn more, watch our Cloud Security and Compliance Best Practices podcast episode.
Finding a credible expert with the appropriate background, expertise, and credentials can be difficult. CompliancePoint is here to help.





