Performing a HIPAA Security Risk Assessment
Under HIPAA, a covered entity or business associate must perform an annual HIPAA Security Risk Assessment. However, the Rule does not provide a detailed roadmap of how to conduct such an assessment. The HIPAA Security Rule only states that covered entities and business associates must “Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity or business associate.”
If your organization is new to HIPAA, security, and risk management, you might be wondering, “How do we perform a risk assessment?”
NIST SP 800-66 is a good reference for organizations that need to conduct an assessment that complies with HIPAA standards. In this article, we’ll explain the steps that are promoted by NIST and widely accepted as best practices in the healthcare sector.
Identify and Locate your ePHI
The purpose of a HIPAA Risk Assessment is to identify and mitigate risks to electronic protected health information (ePHI) your organization holds. Organizations need to know where and how ePHI is created, gathered, stored, processed, and transmitted. Thus identifying all entry points for the data (web portals, paper forms, etc.) and all IT assets that may hold ePHI; and if ePHI is transmitted to any third-party vendors, such as cloud service providers, identify what equipment is used to transmit the data.
This information will allow you to determine the scope of your risk assessment. All locations and network assets that come into contact with ePHI need to be included. All removable media and portable computing devices (e.g., laptops, mobile devices) and medical devices that can store, process, or transmit ePHI also need to be covered. Any remote workforce and external service providers need to be accounted for.
It is worth noting that any individuals or physical assets that touch ePHI and are left out of the scope can result in an incomplete HIPAA risk assessment.
What are the Threats
Organizations need to identify the threats that could put ePHI they possess at risk. Your list of threats should include common cyberattack methods such as phishing, ransomware, malware, and credential theft. Malicious activities from insiders need to be taken into account as well. However, organizations need to think beyond cyber threats when considering how ePHI could be put at risk, such as human error, which can include:
- Data entry mistakes
- Sending PHI to the wrong recipient
- Employees accessing PHI without authorization (intentionally or unintentionally)
- Losing devices that contain PHI
- Failing to properly dispose of documents that contain PHI
Organizations also need to consider how a natural disaster like floods, fires, earthquakes, etc. could impact their ability to protect and access ePHI. Physical security, or the lack thereof, could result in hardware or physical records containing PHI from being stolen or tampered with.
If your organization uses a cloud service, be sure to identify threats associated with its use.
Identify your Vulnerabilities
Organizations need to identify the vulnerabilities in their security programs and network infrastructures that expose them to risks; technical and non-technical vulnerabilities need to be recognized.
Common vulnerabilities include:
- Outdated software
- Weak passwords and/or no multi-factor authentication
- Lack of encryption
- Poor access control to prevent unauthorized users from accessing PHI
- Poor cloud security
- Insufficient HIPAA training for employees
- Inadequate physical security such as locks, alarms, and surveillance cameras
- Not having an incident response plan
Organizations should conduct penetration testing and vulnerability scans at least annually to help identify their security vulnerabilities.
Determine the Likelihood of a Threat
At this point in the HIPAA Risk Assessment, organizations need to:
- Determine the likelihood that a specific threat will occur
- Determine the likelihood that a threat would exploit an identified vulnerability and cause an adverse impact
Organizations can assign a likelihood value to a threat/vulnerability combination, using a “very low” to “very high” scale for the likelihood of the threat occurring and having an adverse impact. They can use this sample chart from NIST 800-66 to assign an overall likelihood rating to a threat having an adverse effect.
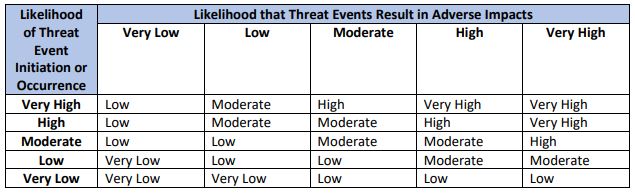
Determining the Impact of an Event
Now it’s time to determine how a threat would impact PHI and an organization’s operations. Impacts that need to be considered include:
- The confidentiality of PHI and the organization’s ability to protect it from unauthorized disclosure
- PHI integrity and the ability to prevent improper modification
- The availability of PHI
- How the threat would impact the organization’s ability to perform its business functions
- Financial costs
- Damage to relationships
- Damage to physical assets and property
- Loss of intellectual property
- Physical, emotional, and reputational harms to individuals
To give the event a score or ranking, qualitative and quantitative methods can both be used to determine the level of impact.
Determining the Overall Risk Level
Assessing the conclusions from the previous steps (identifying threats, identifying vulnerabilities, determining the likelihood of the threat occurring, and determining the impact of the threat) is used to determine the overall risk level associated with threats.
Here is a sample risk-level matrix from NIST.
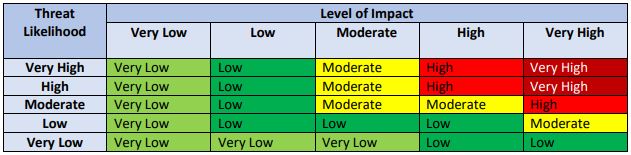
Document your HIPAA Risk Assessment
The results of your HIPAA Risk Assessment need to be documented and shared with organizational leadership. NIST SP 800-30 (pages k1 and k2) provides a sample risk assessment report outline that your organization can use. Make sure that the organization’s management reads and reviews the HIPAA Risk Assessment.
HIPAA Risk Assessment Podcast
To learn more about performing HIPAA security and privacy risk assessments, watch the Compliance Pointers episode below.
CompliancePoint has a team of experts dedicated to helping healthcare organizations comply with all aspects of HIPAA. Contact us at connect@compliancepoint.com to learn more about our services.
Finding a credible expert with the appropriate background, expertise, and credentials can be difficult. CompliancePoint is here to help.





