HITRUST Certification: What to Expect
HITRUST provides a certifiable information security framework (CSF) that allows you to conduct a single assessment to provide assurance to your customers that you are protecting their confidential information. The HITRUST CSF integrates and harmonizes data protection requirements from a variety of sources – ISO, NIST, PCI, HIPAA, COBIT, GDPR – and allows you to tailor the requirements based on your organizational, system and regulatory risk factors.
Obtaining a HITRUST Certification demonstrates to your customers that you have implemented rigorous controls to protect their confidential information. Providing customers with your HITRUST Certification can dramatically reduce the time spent responding to individual security questionnaires and sets you apart from your competition.
The foundation of the HITRUST program is the HITRUST Common Security Framework (CSF), which incorporates numerous relevant regulations and standards into one framework. The HITRUST CSF Certification was developed to provide organizations with demonstrable proof of their commitment to the security of confidential information. The HITRUST CSF is updated at least annually to ensure that organizations address changes in the security requirements.
HITRUST breaks the CSF into 14 Control Categories:
- Information Protection Program
- Endpoint Protection
- Portable Media Security
- Mobile Device Security
- Wireless Security
- Configuration Management
- Vulnerability Management
- Network Protection
- Transmission Protection
- Password Management
- Access Control
- Audit Logging & Monitoring
- Education, Training and Awareness
- Third-Party Assurance
- Incident Management
- Business Continuity & Disaster Recovery
- Risk Management
- Physical & Environmental Security
- Data Protection and Privacy
Within each Control Category, the organization is assigned specific controls based on their risk factors such as organization type, organization size, network design, and geographic location. Each control within the Control Category is scored based on the Control Maturity Requirements and the score for each Control Category must average at least a 62 for the organization to obtain a HITRUST Validated Certification.
Why Should I Consider HITRUST?
- Your client requires HITRUST Certification. Probably the number one reason CompliancePoint clients achieve HITRUST certification is due to customer requirements or requests. HITRUST is required or requested by several major payors and large healthcare provider systems.
- You want a competitive advantage. Obtaining a HITRUST Validated Certification can set you apart from your peers by providing proof of your commitment to protecting confidential information. Unlike just saying you are HIPAA compliant, having a HITRUST Validated Certification provides independent evidence of your commitment to cybersecurity.
- You want to reduce the time required to respond to security questions. Increasingly organizations are performing cybersecurity due diligence on their vendors before entrusting their data to them. HITRUST bills itself as a tool to “certify once, report many”.
What is the Assessment Process?
HITRUST Validated Assessments are performed by the organization seeking certification working with their External Assessor firm. The organization will complete the questionnaire in the HITRUST MyCSF Portal, including the evidence for all the required controls, which is then evaluated by the External Assessor. Once that process is complete, the assessment is submitted to HITRUST for QA review.
While it’s theoretically possible to hire your assessor and immediately begin your assessment process, in most cases, this would not have the desired outcome of obtaining a HITRUST Validated Certification. The CSF is very detailed and complex, and most organizations would want to assess their readiness before investing in a validated assessment.
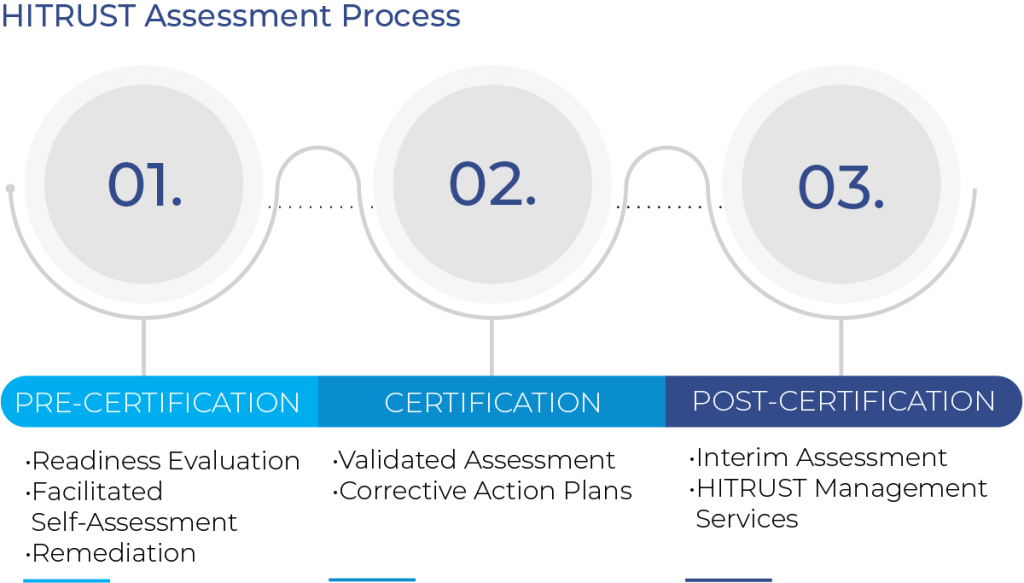
HITRUST Assessment Process
- Pre-Certification
- Readiness Evaluation
- Facilitated Self-Assessment
- Remediation
- Certification
- Validated Assessment
- Corrective Action Plans
- Post-Certification
- Interim Assessment
- HITRUST Management Services
Pre-Certification
CompliancePoint’s Assessment process begins by helping you evaluate your current readiness for HITRUST. We work with you to identify the required controls and determine the status of your policy, process, and implementation evidence for those controls.
We then assist you with a Facilitated Self-Assessment using the HITRUST MyCSF Portal. The HITRUST Facilitated Self-Assessment is designed to give you a clear idea of how your organization measures against your HITRUST CSF Requirements and what gaps you need to remediate to achieve certification.
The Assessment is conducted by utilizing the tools and methodologies of the HITRUST CSF Assurance Program. Your Assessment will be facilitated by experienced HITRUST Certificated CSF Practitioners (CCSFP) who understand the HITRUST requirements to achieve certification. Your Assessor will help you identify the documentation that supports the implementation of your controls and assist you in preparing that documentation for submission to HITRUST for a Validated Assessment.
The Self-Assessment can be submitted to HITRUST, who will give you a formal report which can be provided to your customers as evidence of your progress on the HITRUST certification process. Additionally, the evidence and scores loaded into the Self-Assessment can be transitioned to your Validated Assessment in MyCSF, reducing the time required to complete the Validated Assessment.
- Readiness: Evaluate current status.
- Governance
- Policy/Process documentation
- Self-Assessment: Evaluate control maturity.
- Policy/Process
- Implementation evidence
- Remediation: Provide a GAP Remediation Plan.
- Next Steps
- Timeline
- Resources
Certification
The Validated Assessment will be conducted after completion of the Self-Assessment remediation of any identified deficiencies. The assessment approach is based on HITRUST guidance for assessing the organization’s controls via data gathering techniques, including document reviews, interviews and testing.
Your Assessor will work with you to help you identify and present the strongest documentation possible to support your Certification. The Validated Assessment is then submitted to HITRUST for their review and certification.
HITRUST will perform a review of your assessment to verify it meets the Certification standards. As part of that process, HITRUST may identify individual controls that do not meet their standards even though your assessment as a whole does. Prior to providing you final Certification, HITRUST will require you to develop Corrective Action Plans for those controls. Your Assessor will work with you to create the required Corrective Action Plans for submission to HITRUST.
- Examine
- Policies
- Processes
- Implementation evidence
- Interview + Observe
- Management
- System Owners
- IT Security Personnel
- Test
- System configurations
- Control implementation
Post Certification
Interim Assessment: Your Validated Assessment is valid for a two-year period from the submission date. However, HITRUST requires that you have an Interim Assessment performed by an External Assessor at your one-year anniversary. The Interim Assessment will test 19 controls selected by HITRUST and validate the status of your Corrective Action Plans. Your Account Executive will contact you to set up your Interim Assessment approximately three months before it is due to HITRUST.
HITRUST Management Services: Achieving HITRUST Certification is a significant step. However, in order to maintain your certification, you have to continue to monitor your controls and stay up to date on changes to the HITRUST CSF. CompliancePoint can assist you with this. However, there are ongoing activities that must be done to maintain your certification:
- Corrective Action Plans: The action plan submitted to HITRUST as part of your assessment needs to be completed as indicated prior to your interim and/or validated assessment. Processes need to be implemented to ensure the Corrective Action Plans stay on track to meet the HITRUST requirements.
- Continuous Monitoring: HITRUST has a number of controls that require ongoing monitoring to be performed and documented. The table below summarizes just some of the monitoring activities.
- Ongoing Monitoring
- Malicious Code Alert Investigation
- Compliance Program Monitoring
- Blacklisted & Whitelisted Software
- Email Monitoring
- Testing of Monitoring & Detection
- Third Party Due Diligence
- Visitor Log Reviews
- Media Management
- Backup Testing
- Commercial Product Security Assessment
- Quarterly Monitoring
- Wireless Access Scanning
- User Access Scanning
- Physical Access Validation
- Remote Access Validation
- Application Vulnerability Testing
- Annual Monitoring
- Policy & Procedure Review
- Governance Reporting
- Technical Compliance Reviews
- Vulnerability & Penetration Testing
- Security Training
- Incident Response Plan Testing & Review
- Security Program Audits
- Risk Assessments
- Evaluation of Training Effectiveness
- Bi-Annual Monitoring
- Network Diagram Revision
- Password Validation Review
- Ongoing Monitoring
- HITRUST Updates: HITRUST updates the CSF at least once a year to reflect changes in the security environment. Those changes may result in new controls or changes to existing control requirements, which will need to be addressed prior to your next validated assessment.
CompliancePoint’s HITRUST Assessment Team has extensive experience in helping organizations achieve and maintain HITRUST Certification. Additionally, our assessors have worked in the industry and understand your challenges, which allows them to help you find effective ways to meet the HITRUST requirements. The team has been trained, tested, and certified by HITRUST, PCI Security Standards Council, the Information Systems Audit & Control Association (ISACA) and are listed as HITRUST CSF Assessors, HITRUST Quality Professionals, Qualified Security Assessors (QSAs) and Certified Information Systems Auditors (CISAs) in good standing on their respective websites. If you are interested in how we can help, please reach out to us at 855-670-8780 or connect@compliancepoint.com
Finding a credible expert with the appropriate background, expertise, and credentials can be difficult. CompliancePoint is here to help.